Title of the paper:-
On The Design Of An Intelligent Sensor Network For Flash Flood Monitoring, Diagnosis And Management In Urban Areas.Position Paper
M. Anconaa,∗ , N. Corradib, A. Dellacasaa , G. Delzannoa , J.-L. Dugelayc , B. Federicid, P. Gourbesvillee , G. Guerrinia , A. La Cameraa , P. Rossof , J. Stephensg, A. Tacchellaa , G. Zolezzih.
Find out what you can about the author(s):-
it gives the full detail of the author and universities from which it belongs to.this information is given below.


Did the abstract tell you the three things I said it should? If not, what did it tell you?
Yes
“In this article author find the reasons behind the climate changes in Europe show an increased frequency and intensity of heavy rainfalls and flash floods in urban areas.”
What the authors/researchers did and what they discovered?
the author purpose an propose an intelligent sensor system based on a new sensing methodology, relying also on 3D map reconstruction techniques, for computing with high precision, in real-time and without human intervention the parameters needed for stream-flow computation: water levels, morphology of the streams of all potentially flooded areas by each controlled stream. The collected data will be continuously transmitted, through a communication infrastructure, to software agents designed to compute the stream-flow and to quantify the spatial distribution of flood risk for each controlled watershed. The computed risks, together with other data coming from other sources (barometric sensors, camera operators of public organizations, emergency agencies, private citizens), will be analyzed by a diagnostic decision system implementing a risk-alert scheduling strategy. This system will be able to diagnose the health state of the controlled environment and to define specialized alarm levels for each potentially interested area that will be used to alert all citizens (ubiquity) locally present (alerting locality).
What seems to be the research question(s) they were trying to answer or the purpose of the paper?
This article provides the information about the design and working of intelligent sensor system which find out the readings about the climate change.
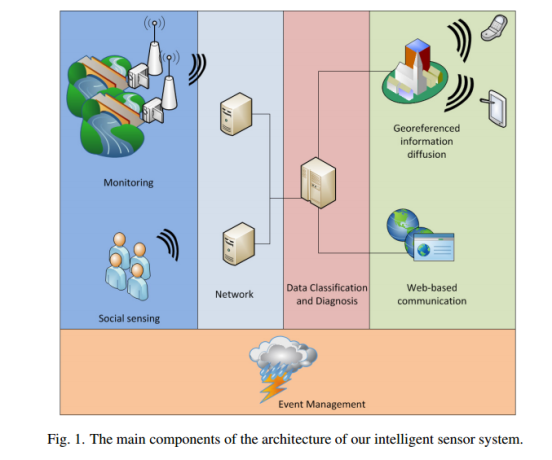
Briefly describe the method(s) they used to answer the questions(s) – did this seem like a good way to try to answer the question? Why?
They did a case study on climate changes and the natural disasters occurs in the urban areas.they explain about the design and working of an artificial intelligence sensor system by which they note the readings about the climate changes before the disaster happens.Yes, Because when it comes to a new concept, needs to find out the existing characteristics of the technology we use to enhance those in the new concept. Therefore a case study will make a good way to try to answer these research questions.
Did you agree with what they wrote in their conclusion? Do the results seem credible to you?
Yes i totally agree with the conclusion because everything related to the sensor and the advantages of it are mention in the conclusion.it also talk about the disadvantages of the system like it required a high definition version of it.in the end i said I agree with them and results seems to be credible at this stage.
Do the references suggest that the paper is credible?
yes
Briefly describe two things that you learnt from the paper
i learnt so many things in the paper.its a fruitful knowledge.i mention some below.
I learnt that“Features like buildings, constructed river banks or roads have a great effect on flow dynamics and flood propagation and only high-resolution input data can solve the purpose that relates to the systems topography …omissis… Differences of a few meters can means a lot in loss calculations in urban areas. LiDAR has brought this level of detail to the industry allowing for much more accurate flood prediction models to be create”
Does this paper help you to know more about your interest area?
Yes because i love to find the relation between the computer and the nature these type of things make me excited to read. because i want to know about the latest techniques by which we find the more facts about the mother nature.no issue weather it is related to biology zoology or geography.i only want to learn about how technology related to the nature.